
April 17th, 2024
The Move from Vulnerability to Exposure Management

April 9th, 2024
Threat Exposure Management: Implementation Of Best Practices

April 2nd, 2024
Navigating the Rising Tide of Data Exfiltration

March 26th, 2024
Threat Exposure Management: A Shift in Strategy

March 19th, 2024
What Goes Around Comes Around: How to Protect Yourself Against Evolving Threats

March 12th, 2024
Cymulate Research Highlights the Path to Proactive Security

March 6th, 2024
Threat Exposure Management: Continuous Monitoring and On-Going Assessment

February 29th, 2024
Introduction to Threat Exposure Management and its Outcomes
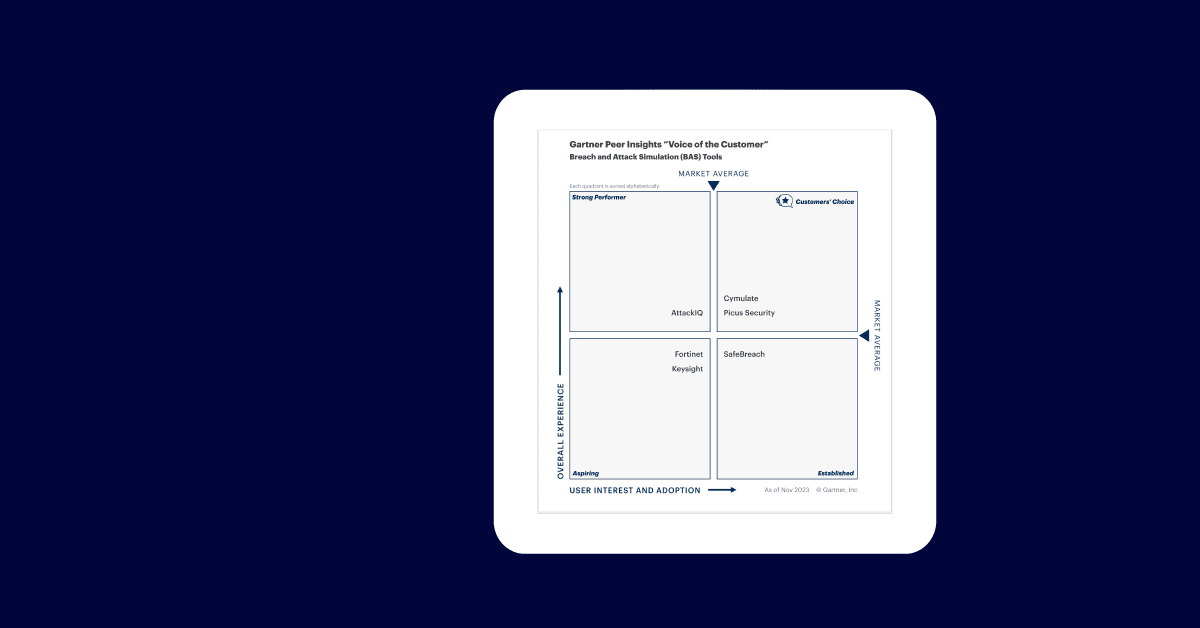
February 26th, 2024
Cymulate Named a Customers’ Choice by Gartner® Peer Insights™ 2024 VOC

February 22nd, 2024
ScreenConnect Joins AnyDesk to Highlight Threats to Remote Access Tools

February 22nd, 2024
Cymulate Named ASM Leader in GigaOM Radar Report

February 14th, 2024
EDR Bypass Part 2: Techniques

February 8th, 2024
EDR Bypass Part 1: Understanding Today’s Tools

February 1st, 2024
Cyber Threat Breakdown January 2024

January 23rd, 2024
Closing Out the CTEM Journey with Validation and Mobilization

January 16th, 2024
Using CTEM to Engage in Scoping, Discovery, and Prioritization of Cyber Challenges

January 9th, 2024
Cymulate Threat Research: Security Monitoring Efficacy of Cloud-Native Kubernetes

January 3rd, 2024
Cyber Threat Breakdown December 2023

December 14th, 2023
Old Threats, New Tricks: Why Legacy Malware Keeps Infiltrating Networks

December 7th, 2023








